EU Cyber Resilience Act
The cyber resilience act will set requirements to products that have so-called digital elements and that are put on the EU market. The goal of the act is to improve the cybersecurity of products that have digital elements in the EU market by setting minimal requirements on the product manufacturers, importers, and distributors. In most cases, the term digital element refers to software, but the act is relevant also hardware products such as field-programmable gate array (FPGA) based products.
Timeline
As the Cyber Resilience Act is an act rather than a directive, it will be effective legislation directly, rather than through national laws that would have to be prepared by the EU member states. There is an agreement about the contents of the act in the union, so it is expected to enter into force during the first half of 2024. There is a 21-month transition period for the notification responsibilities of the act, and a 36-month transition period for the other requirements.
In terms of the planning schedules of a product development company, the first deadline set by the transition periods is that you should be prepared to have an arrangement to organise your vulnerability handling activities up and running roughly by early 2026 at the latest. For the other requirements, the deadline is expected to be in the first half of 2027. This may sound like a lot of time, but given the profound impacts of the act, the best time to start working towards these deadlines is right now.
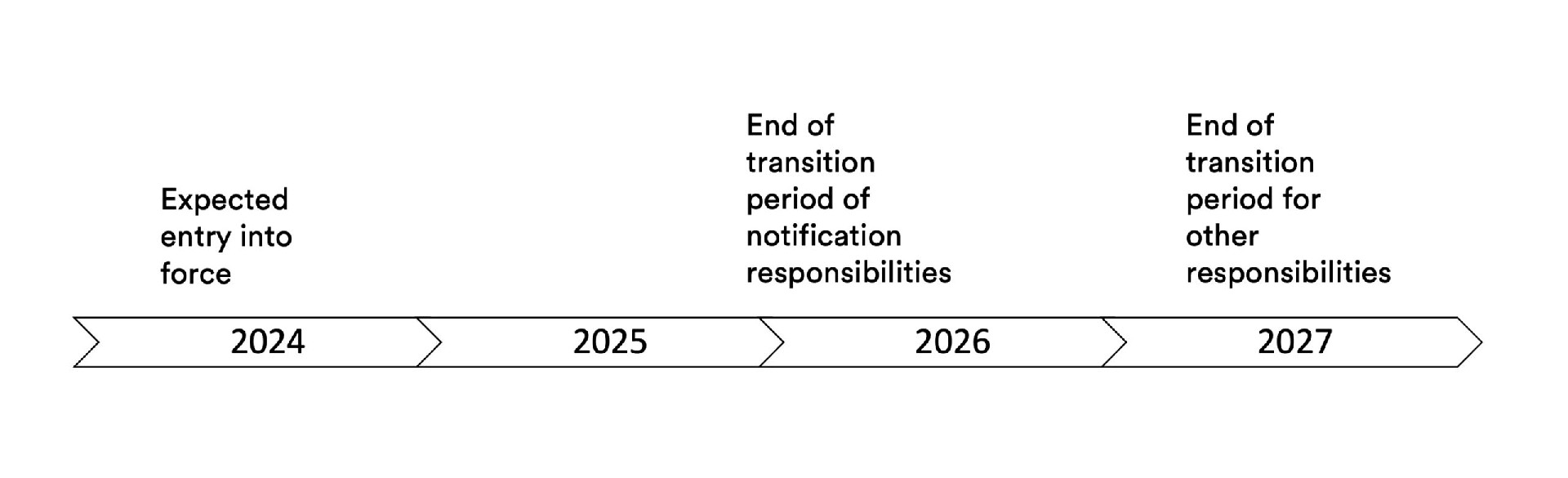
The act will not affect products that have been put on the EU market before the act has become effective. So, you might be tempted to schedule a long term supported product release at the end of 2026 and try not to make significant changes that would trigger the requirements of this act. However, I would advise not to rely on this wiggle room too much. The customers and the market may start requiring an appropriate level of cybersecurity, and frankly speaking users, citizens and companies deserve to have products, where any software-related cybersecurity risks are adequately managed.
Direct Impacts
The requirements of the act are relatively straightforward, and we encourage you to read the actual text of the act once the final text becomes available. What’s clear from the outset is that everything starts from a risk assessment that the manufacturer must conduct. The other essential requirements should be implemented based on the results of the risk assessment and proportionally to the risks.
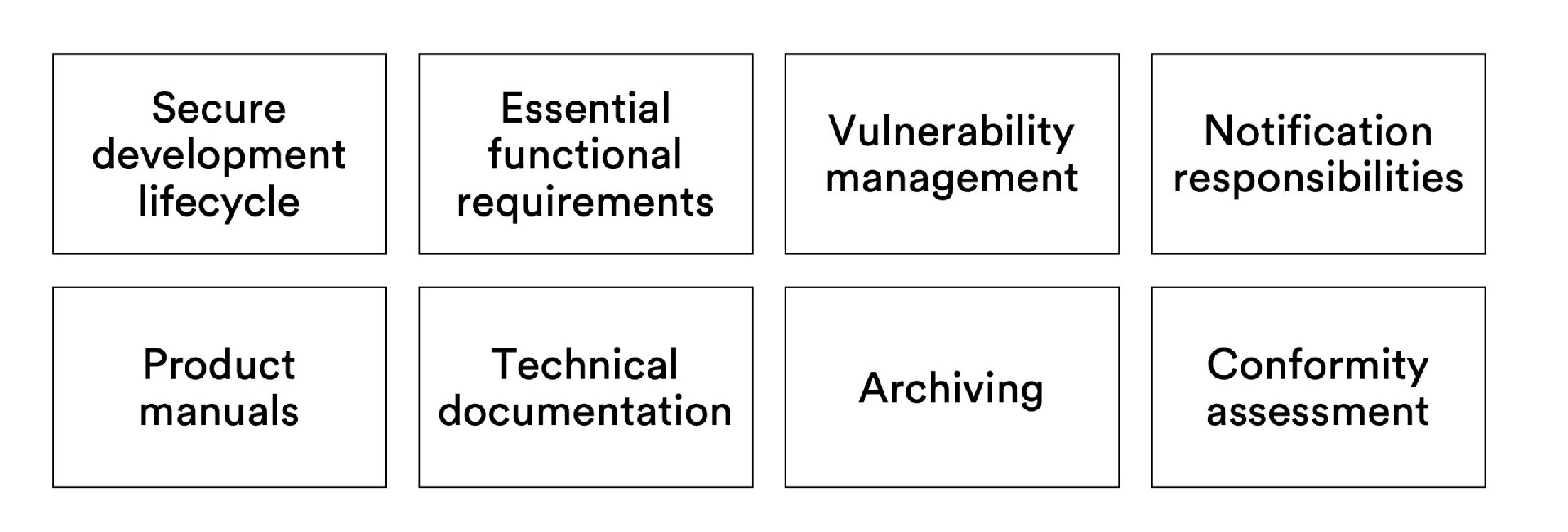
SDL Process: Product development must apply a design, development, manufacturing, and maintenance process that ensures an appropriate level of cybersecurity. There is a requirement to apply effective and regular tests and reviews. In practice, you need to ramp up a Secure Development Lifecycle (SDL) process.
Essential functional requirements: Products must meet a small set of essential requirements, again proportionally to the risks and where applicable. The requirements are short, and you should read them directly from Annex I of the act. They include:
not having exploitable vulnerabilities when the product is put on the market,
a secure by default configuration,
support for security updates including automatic updates where applicable,
access control,
confidentiality and integrity of data,
minimisation of data,
protecting the availability of essential functions after incidents, which includes protections against denial-of-service attacks,
minimise the negative impact by themselves or connected devices on the availability of services provided by other devices or networks,
limiting attack surfaces (hardening),
reducing the impacts of incidents with appropriate exploitation mitigation mechanisms,
cybersecurity monitoring, and
possibility to remove data, for example when the product is being disposed.
Vulnerability handling is a major area in the Cyber Resilience Act. Product manufacturers must:
draw up a software bill of material (SBOM),
address and remediate vulnerabilities promptly. This would typically require providing a software update,
share and publicly disclose information about fixed vulnerabilities,
have a policy on coordinated vulnerability disclosure,
share information and set up contact channels for reporting vulnerabilities,
provide a software update distribution mechanism so that fixes can be mitigated quickly and where applicable automatically, and
provide free-of-charge security updates and documentation.
The act includes responsibilities to notify authorities in case of actively exploited vulnerabilities or severe incidents that have impact on the security of the product. An early warning notification must be submitted within 24 hours of becoming aware of the issue, the actual notification within 72 hours and a final report of handling the issue within 14 days (for actively exploited vulnerabilities) or one month (for incidents).
In terms of documentation, the act requires product manuals to include certain security related guidance to the users, such as secure installation, integration, operation, and disposal instructions.
The product development team must also write an extensive set of technical documentation that includes for example the risk assessment, architecture and design specifications, vulnerability handling documentation and copies of the cybersecurity test plans and test results. The technical documentation does not have to be public, but it may have to be provided to market surveillance authorities.
The product manufacturer will also have to conduct an EU conformity assessment procedure. There are different ways to do this, and the required method depends on the criticality of the product. The original Cyber Resilience Act proposal from the EU commission included two classes of critical products. To our knowledge, the final act will still have the same basic structure, but the definitions of the classes will be different from the original proposal. This is an area where we recommend waiting for the final text before making too many planning assumptions. Nevertheless, the requirements of the act will concern all products that have digital elements, only the required method of the EU conformity assessment will be different for critical products.
Finally, product manufactures should archive the product releases, SBOMs, product manuals, technical documentation, and the statement of conformity for 10 years.
数据合规创造业务价值
给我们一个开始了解需求的机会,共同来保护贵司的业务。
Copyright © 2025 Shanghai Digital Shell Information Technology Co., Ltd All Rights Reserved.

